Adaptive Security for 5G Edge Networks
The rise of edge networking and distributed applications exponentially increases the attack surface for both the enterprise and Telecom infrastructure. EnterpriseWeb and Fortinet have partnered on award-winning solutions that continuously observe, manage and secure 5G multi-access edge computing (MEC) end-to-end. By Dave Duggal, founder and CEO of EnterpriseWeb and Ronen Shpirer, Director, Telco Solutions Marketing at Fortinet.
The Telecom industry is following in the footsteps of the Cloud providers, seeking to expose APIs to developers so they can design applications that can dynamically access and control network infrastructure. It opens the door to network-aware business applications that can dynamically scale resources up and down on-demand to ensure optimized performance, while maintaining efficiency. This is particularly attractive at the edge, where resources are constrained and local processing is limited.
Of course, with great power comes great responsibility. Exposing network data and controls to the Developer community opens the network to a new set of exploits. Integrated solutions from EnterpriseWeb and Fortinet close the gaps to protect both the business applications and the Telco infrastructure from exploits.
While there are emerging standards for developer-facing APIs (e.g., Linux Foundation CAMARA; GSMA Open Gateway; ETSI Network Exposure Function), there is no common model or shared library to support their implementations. This is a roadblock to adoption and leads to one-off implementations, which makes management, including security management, more difficult.
EnterpriseWeb Intelligent Orchestration
EnterpriseWeb offers an AI-enabled no-code platform. The cloud-native automation platform can deploy at the data center, in the cloud or at the edge. At only 50mb, the platform provides lightweight, low-latency, high-performance middleware capabilities in an edge-optimized form factor to keep processing local. EnterpriseWeb nodes can also connect in a peer-to-peer network to form a mesh network or “application fabric”.
EnterpriseWeb uses graph domain models to support intelligent orchestration. The graph efficiently provides the necessary context to optimize interactions. It acts as a single source of truth so developers can rapidly design smart, network-aware business apps that dynamically and continuously optimize latency, bandwidth and resources.
The platform provides a consistent developer experience, simplifies and automates IT tasks, and enables centralized management. As part of its role, the intelligent orchestrator continuously observes and manages all deployed services and the underlying infrastructure to ensure security, scalability and performance.
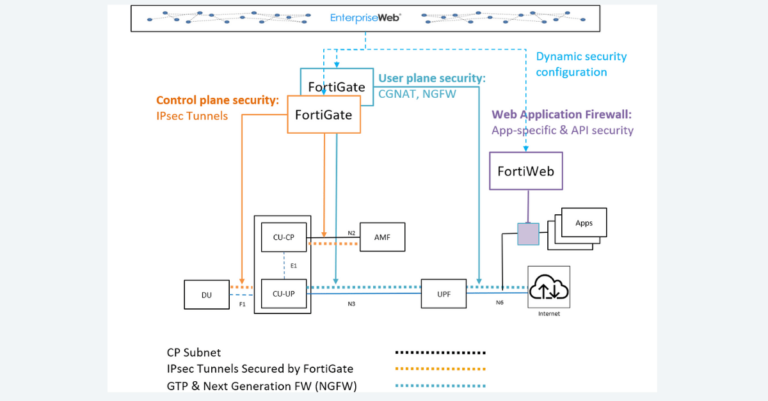
In the joint solution, Fortinet FortiWeb provides application and API security and Fortinet FortiGate provides Next Generation Firewall and 5G cybersecurity, securing all the endpoints and protecting user and control plane traffic.
Since application workloads and deployment environments vary, EnterpriseWeb dynamically configures FortiWeb and FortiGate so they are optimized for each use-case. Post deployment, EnterpriseWeb continues to monitor application activity and network usage and reconfigures Fortinet’s products to maintain security levels based on real-time network context. Static security configurations present an unacceptable risk.
Dynamic Security Configuration
- EnterpriseWeb identifies assigned CP Subnet(s) via CNI Mapping (at time of initial deployment) and for all Function / Component Pods and Containers identifies virtual port assignments / IPs (translated from OpenShift APIs)
- EnterpriseWeb identifies SDN level IPsec Tunnels (Point-to-Point) between components (from underlying CNI, Service Mesh, Network OS) and dynamically configures FortiGate to monitor and secure each / all such tunnels, adding and removing as the service evolves (scales, heals, etc.).
- As security demands change, EnterpriseWeb scales FortiGate and/or adjusts networking to prioritize traffic to reflect evolving application behavior
Fortinet Adaptive Security
Fortinet’s market-leading security products also leverage AI to continuously optimize their own behavior. In addition to traditional negative and positive security models (attack signatures, IP address reputation, protocol validation, etc.), FortiWeb applies a second layer of machine learning-based analytics to detect and block malicious anomalies while minimizing false positives. Fortinet’s Adaptive Security ensures that protections are continuously responding to the volatile network and changing threats.
Together, EnterpriseWeb and Fortinet are providing an intelligent SASE solution that provides end-to-end protection spanning network infrastructure (control plane), network traffic (user plane), and application security. To see the advanced capabilities in action, watch the replay of their latest demo in collaboration with Intel, Microsoft and KX – “Secure Dev-centric Networking with CAMARA APIs”.