From Pilot to Operation: The Role of Autonomous Operations in Private 5G/LTE Growth
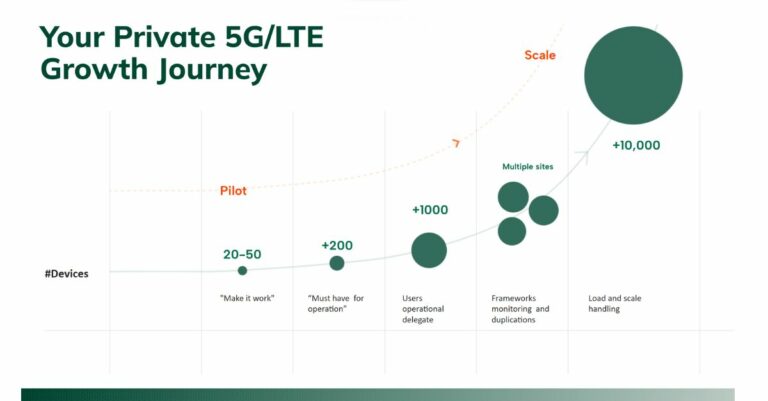
The fast-evolving landscape of private 5G/LTE networks showed a move last year toward operational networks after several years of pilots and trials. A new player now enters the picture: operation teams. As the network users, the key to private 5G/LTE growth and scale depends on this player’s technology adoption.
Autonomy in Private Cellular Networks: A New Era
Operation teams can achieve real adoption only if they have autonomous operations. This is the key to providing flexibility, ease of use, freedom, and support for their dynamic operational needs. But how can autonomous operations of a private cellular network coexist with support for the company’s security and networking frameworks?
Delegating the Keys to the Network
The key to unlocking the true potential of private 5G/LTE networks lies in the delegation of network operations from the network owner/carrier (classically responsible for cellular network operations) to the users of the network and its connected devices. Empowering these stakeholders with the freedom and flexibility to manage the network transforms the cellular network from a static infrastructure into a dynamic, adaptive ecosystem that can seamlessly accommodate evolving use cases and requirements.
The device is the critical operational unit of the private cellular network, so smooth operation necessitates autonomous processes for the full device lifecycle, from device onboarding (e.g., SIM provisioning, device activation, QoS, proper networking, context-based security policy allocation aligned with existing frameworks) to daily monitoring to root-cause analysis of problems. All this while keeping the network as a whole monitored, load-balanced, and efficient.
IP networks have had such solutions for years, but cellular network infrastructure wasn’t designed to support this type of autonomy, especially when it also needs to comply with stringent security frameworks and networking standards.
Let’s examine the functional capabilities needed for the efficient, secure, and autonomous operation of the private cellular network throughout the device lifecycle.
1. Automatic Device Onboarding
A fully operational autonomous private cellular network should provide an authorized device user the freedom to add a new device to the network without the need for intervention by the network management team. The functions necessary for device onboarding include:

Smooth operation necessitates autonomous Device Onboarding processes for the full device lifecycle.
SIM provisioning
The authorized user should have the ability to easily add a new SIM to the network with all the proper information.
Device activation
Once the SIM is provisioned, the authorized user should be able to match a SIM to a device, lock it to the device (if necessary), connect the device to the network, and choose the relevant connectivity profile to support the intended device use.
Device networking allocation
Once the device can connect to the network, connectivity specifics such as QoS, relevant APN roles, IP range or static IP, etc. should be automatically assigned.
Device authorization and security policy and access privilege allocation
Autonomous operations tools should automatically assess the device context and add the device to relevant policy groups so it will inherit proper use privileges, including micro-segmentation, access limitations, and communication pattern boundaries.
And critically important…
All the above functions should integrate smoothly with the platforms and processes used for the other enterprise networks, such as IT and OT.
2. Day-to-day Network Monitoring and Hygiene
Autonomous device onboarding is just the beginning. To have successful network operations that continue to give value long-term, you need to have an unobstructed view of the network’s big picture and the ability to understand, analyze, and apply what you observe. The functions necessary for network monitoring and hygiene include:

Smooth operation necessitates autonomous Unified Orchestration & Daily Monitoring processes for the full device lifecycle.
Functional assessment, network efficiency, and load management
Your network team should be able to easily find out the current load on the network, the potential for adding new use cases, and areas that need to be shored up.
They should also have the ability to assess the performance of network components or devices, empowering them to make informed decisions about the current value provided by vendors and where and how to optimize performance.
Asset management
At the simplest level, authorized users should be able to identify and locate network devices. Effective network management also requires inventory management: evaluating the performance of your current inventory and predicting inventory needs.
Inter-team common language
Different functional teams think about cellular network devices differently.
To the operations team, the device is a physical asset; to the security team, it is associated with its network identifier (e.g., IP); to the cellular team, it is its cellular identifier (e.g., IMEI, IMSI). However, effective collaboration between functional teams in both routine and emergency tasks requires a common language. A fully operational network should provide each network device with one universal identifier that matches and connects all the different identifiers, providing an organization-wide common language for communicating about network devices.
Risk reduction and network hardening
Cellular networks do not inherently have the ability to create isolated zones that help contain potential breaches and limit the impact of cyber threats. Yet, aligning the private cellular network with industry standards and ensuring compliance are essential for robust security.
To fulfill the role of a fully autonomous operational network, private 5G/LTE networks need the ability to secure devices with Zero Trust policies following your segmentation model of choice and block unauthorized communication leveraging third-party enforcement tools. For a cohesive enterprise network setup, you should be able to use the same policies and tools, such as firewalls, across all networks: IT, OT, and public and private cellular.
3. Root Cause Analysis When Things Go Wrong
Private cellular network problems can range from innocuous troubleshooting of a device’s lack of connectivity to addressing an intense cyberattack. Either way, the order of the day is to track down the root cause as quickly as possible and move to mitigation or remediation.

Smooth operation necessitates autonomous Threat Prevention processes for the full device lifecycle.
Reduce downtime through efficient troubleshooting
Since operation uptime is critical to profitability, a fully functional autonomous private cellular network must have a way of quickly backtracking from an initial manifestation of a problem and zeroing in on the device or network component that is the source of the problem. The ability to observe the network data from different perspectives, including (but not limited to) device location, operational use, and network behavior (both IP and cellular) is important for this root cause analysis functionality.
Detection, investigation, and mitigation of anomalous events
In the cyberattack domain, where timely detection of abnormal behavior is crucial, enterprises require the ability to detect and respond to malicious activities or misconfigurations quickly. The response time should be measured in hours and days – not weeks and months. Root cause analysis tools and automation are needed to investigate events, reduce real-time alert investigation time, and present a network and cellular events history log for any given device.
Provide information for both network and cyber operations
To ensure the most effective root cause analysis processes, enterprises require a solution that extends existing IT and OT network security and compliance practices to private 5G/LTE networks. Such a solution would provide the critical missing link between the 5G/LTE packet core and the security and operations tools and practices used to protect and manage IT and OT networks. Critical capabilities would include enhancing the visibility of existing IT/OT asset management tools with additional information regarding cellular assets, sending alerts to existing security monitoring tools to enable immediate response, and creating a single source of truth for cellular asset management.
Making Good on the Promise of Private Cellular Networks
When it comes to private 5G/LTE networks, the transition from promising pilot to value-adding enterprise network requires a solution for autonomous operation. Only by transferring network management from owners to authorized device end users can the scalability, operational flexibility, and dynamic adaptability promised by private 5G be attained.
The achievement of autonomous operation, however, hinges on three key capabilities: seamless device onboarding, day-to-day monitoring and hygiene, and effective root-cause analysis when issues arise. These capabilities demand a robust framework that can both orchestrate the new private cellular network components and interfaces and also integrate with existing operational processes and platforms, thus ensuring cohesive and efficient autonomous operation.
To learn more, visit https://onelayer.com/creating-effective-automated-security-ecosystem-in-private-cellular/ and to read additional related content on Onelayer, visit https://tecknexus.com/keyword/onelayer/