The private network market is expanding rapidly as enterprises scale their private 5G/LTE deployments across industries like utilities, manufacturing, and oil & gas. Companies that began with single-site proofs of concept are now rolling out private networks on a larger scale, tackling challenges in security, IT integration, and SIM provisioning. ...
Home » 5G Magazine » Security for Public and Private Networks | 5G Magazine » Top 30 – Global Security Startups
Top 30 – Global Security Startups
Who are the global security startups that are innovating to solve the security challenges, including protecting public and private networks?
Log In or Register to Access This Article
Login
Register
Feature Your Brand in Upcoming Magazines
Showcase your expertise through a sponsored article or executive interview in TeckNexus magazines, reaching enterprise and industry decision-makers.
Related Magazine Content
Explore NTT DATA’s role in advancing private networks through enterprise 5G solutions, Edge AI, and Network-as-a-Service (NaaS). Learn how these technologies address digital transformation, operational efficiency, and security while offering businesses flexible, scalable, and reliable solutions tailored to their needs. ...
Award Category: Excellence in Private 5G/LTE Networks
Winner: Nokia
Nokia has been recognized with the TeckNexus 2024 Award for "Excellence in Private 5G/LTE Networks" for its transformative solutions that drive industrial digital transformation. Utilizing advanced technologies such as Nokia Digital Automation Cloud (DAC) and Modular Private Wireless (MPW), ...
Award Category: Excellence in Neutral Host Networks
Winner: Celona
Partners: Del Conca and T-Mobile
Celona’s innovative 5G LAN and Neutral Host solutions have been recognized with the TeckNexus 2024 Award for "Excellence in Neutral Host Networks" for transforming connectivity and operational efficiency at Del Conca USA, ...
Award Category: Excellence in Private Network Startups
Winner: GXC
GXC’s ONYX Platform, powered by Cellular Mesh technology, delivers scalable, seamless, and secure communication across industries. Recognized with the TeckNexus 2024 Award for "Excellence in Private Network Startups," GXC's proprietary Cellular Mesh technology and its ONYX Platform have established ...
Award Category: Excellence in Private Network Security
Winner: OneLayer
OneLayer’s innovative Zero Trust and Zero-Touch automation solutions provide unmatched security, visibility, and scalability for private LTE/5G networks. This approach has earned OneLayer the prestigious TeckNexus 2024 Award for "Excellence in Private Network Security," recognizing their contributions to safeguarding ...
Award Category: Private Network Excellence in Generative AI Integration
Winner: Southern California Edison (SCE) & NVIDIA
Southern California Edison (SCE), in collaboration with NVIDIA, has been honored with the TeckNexus 2024 Award for "Excellence in Private Network AI and Generative AI Integration" for their transformative work in modernizing ...
Award Category: Private Network Excellence in System Integration
Winner: L&T Technology Services (LTTS)
Partner: Ericsson, Athonet (HPE), Indian Mobile Operator
L&T Technology Services (LTTS) has been recognized with the prestigious TeckNexus 2024 Award for "Private Network Excellence in System Integration" for its advanced Private 5G integration ...
Award Category: Private Network Excellence in Network Assurance
Winner: Anritsu
Partner: SmartViser, Major European Airline
Anritsu has been recognized with the TeckNexus 2024 Award for "Private Network Excellence in Network Assurance" for its outstanding achievements in ensuring private 5G/LTE network performance and reliability. This award highlights Anritsu’s ...
Award Category: Private Network Excellence in Sustainability
Winner: Nokia
Nokia’s innovative Private Wireless Sustainability Calculator has been recognized with the 2024 TeckNexus "Private Network Excellence in Sustainability" award for its transformative impact on industrial, environmental and social sustainability. This first-of-its-kind tool enables industries to measure, optimize, and monetize ...
Award Category: Private Network Excellence in Innovation
Winner: Fiducia Sports AI
Fiducia Sports AI has been recognized with the TeckNexus 2024 Award for "Private Network Excellence in Innovation" for transforming fan engagement in the sports and entertainment industry. By leveraging artificial intelligence (AI), augmented reality (AR), and the ...
Award Category: Private Network Excellence in Manufacturing
Winner: Ericsson
Ericsson has been recognized with the TeckNexus 2024 Award for "Private Network Excellence in Manufacturing" for its transformative work at the USA 5G Smart Factory in Lewisville, Texas, and global deployments such as the Smart Factory Innovation Centre in ...
Award Category: Private Network Excellence in Sports and Events Venue
Winner: NTT DATA
Partner: Cisco
NTT DATA, in partnership with Cisco, has transformed RAI Amsterdam into a smart, connected venue with the deployment of a private 5G network, earning the 2024 TeckNexus "Private Network Excellence in Sports ...
Award Category: Private Network Excellence in Warehouse and Logistics
Winner: GXC
GXC’s deployment of its innovative Onyx LTE private cellular network at a large-scale poultry processing facility has earned the prestigious TeckNexus 2024 Award for "Private Network Excellence in Warehouse and Logistics." This transformative project revolutionized connectivity and ...
Award Category: Private Network Excellence in Mining
Winner: Ericsson
Ericsson has been recognized with the TeckNexus 2024 Award for "Private Network Excellence in Mining" for its innovative application of private 5G technology to transform mining operations. This accolade highlights Ericsson’s leadership in modernizing the mining sector through high-speed, ...
Award Category: Private Network Excellence in Airports
Winner: Ericsson
Partner: Purdue University & Saab
Ericsson, in collaboration with Purdue University and Saab, has been honored with the 2024 TeckNexus Award for "Private Network Excellence in Airports" for deploying a private 5G network at Purdue University Airport, transforming ...
Award Category: Private Network Excellence in Education
Winner: InfiniG
Partner: Parkside Elementary School, Intel, AT&T, and T-Mobile
InfiniG’s Mobile Coverage-as-a-Service (MCaaS) solution has earned the 2024 TeckNexus "Private Network Excellence in Education" award for its transformative impact on student safety and connectivity at Parkside Elementary in ...
Award Category: Public/Private Network Excellence in Healthcare
Winners: LifeSigns, floLIVE & Hetrogenous
LifeSigns, in partnership with floLIVE and Hetrogenous, has been recognized with the TeckNexus 2024 Award for "Private Network Excellence in Healthcare" for their LifeConnect 5G IoT-powered Connected Ambulance Solution. This transformative technology enhances emergency medical response ...
Award Category: Private Network Excellence in Public Safety
Winner: Cumucore
Partner: Ripsim, Mosolabs, Starlink
When Hurricane Helene struck Western North Carolina, it left behind severe physical destruction and a critical communication crisis, isolating communities from essential resources and emergency services. In response, Cumucore, in collaboration with Ripsim, ...
Award Category: Private Network Excellence in Agriculture
Winner: Invences &
Partner: Trilogy Networks
Invences Inc., in collaboration with Trilogy Networks, has been recognized with the 2024 TeckNexus "Private Network Excellence in Agriculture" award for their pioneering deployment of a private 5G network tailored to transform farming ...
Award Category: Private Network Excellence in Smart Cities
Winners: NTT DATA & Nokia
Partner: City of Brownsville
NTT DATA, in partnership with Nokia, has received the prestigious TeckNexus 2024 award for "Private Network Excellence in Smart Cities" for being selected to deploy a private 5G network in ...
Award Category: Private Network Excellence in Construction
Winners: Samsung & NAVER Cloud
Partner: Hoban Construction
Samsung and NAVER Cloud have been recognized with the 2024 TeckNexus "Private Network Excellence in Construction" award for their deployment of a private 5G network at Hoban Construction’s large-scale apartment project. This ...
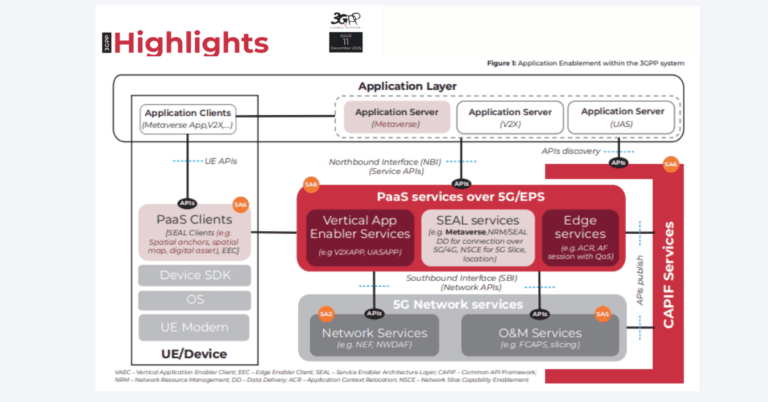
Explore the evolving world of 5G: The roles of SaaS, APIs, AI, and Cloud Platforms in shaping the future of private network management. ...
Explore how eSIM impacts global connectivity, offering flexibility, security, and eco-friendly solutions for telecom. ...

Brand Connect
Amplify Your Brand & Boost Your Business
- Thought-Leadership Management
- Magazine Article
- Executive Interviews
- Whitepapers
- Research Reports
- Custom Research
- Blog Series
- Webinars
- Podcasts
- Advertorials
- Display Ads
- Event Partnership