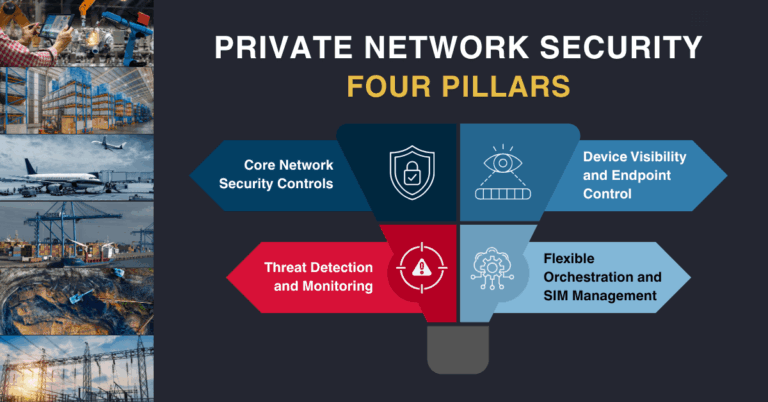
Telecommunications networks form the backbone of global digital connectivity, supporting billions of users, businesses, and critical infrastructures. As networks become more complex and interconnected, they are increasingly targeted by cyber threats, including data breaches, network intrusions, and AI-specific attacks such as adversarial manipulation and model inversion.
Traditional security approaches are struggling to keep pace with evolving threats. AI-powered security solutions provide telecom operators with the ability to detect threats in real-time, automate responses, enhance fraud prevention, and safeguard sensitive data. This article explores how AI is transforming telecom security by mitigating risks, ensuring regulatory compliance, and securing the AI lifecycle.
1. AI-Driven Threat Detection: Strengthening Network Defenses
One of the greatest challenges in telecom security is the detection of hidden cyber threats. Hackers are now leveraging telecom-specific protocols and infrastructure vulnerabilities to bypass traditional security mechanisms. AI enhances threat detection by:
- Real-time anomaly detection: AI can analyze network traffic and user behavior to flag suspicious activities such as unauthorized access, lateral movement, and data exfiltration.
- Predictive threat modeling: AI predicts emerging attack patterns using historical data, allowing telecom operators to preemptively strengthen their defenses.
- AI-enhanced intrusion detection (IDS): AI-driven IDS systems continuously monitor network activity, reducing false positives and enabling faster responses to potential breaches.
- Behavioral analysis for insider threats: AI can identify deviations in employee and system behavior, detecting potential insider threats or compromised credentials before significant damage occurs.
By continuously monitoring and analyzing network behavior, AI reduces the time attackers can remain undetected, limiting damage and preventing major security breaches.
2. Mitigating AI-Specific Cyber Threats
As AI systems become integral to telecom networks, they introduce new security risks. Cybercriminals have adapted their attack strategies to target AI models, data pipelines, and telecom infrastructure. Key risks include:
- Data Poisoning: Attackers manipulate training data to degrade AI model performance, causing misclassification and incorrect security decisions.
- Adversarial Attacks: AI models can be tricked into making incorrect predictions by introducing small but strategic modifications to input data.
- Model Inversion Attacks: Hackers attempt to reverse-engineer AI models, extracting sensitive training data and proprietary algorithms.
AI-Based Defenses Against These Risks
- Secure AI training processes that ensure the integrity and authenticity of data sources.
- Adversarial defense mechanisms that detect and mitigate manipulation attempts.
- Federated learning and encryption techniques that protect AI models from exposure.
By implementing these measures, telecom companies can fortify AI-driven security systems and prevent attackers from exploiting AI vulnerabilities.
3. AI in Fraud Prevention and Identity Protection
Fraud is a persistent issue in the telecom industry, resulting in billions of dollars in annual losses. AI significantly enhances fraud detection and prevention by:
- Monitoring real-time transactions to detect unusual spending or SIM swap fraud.
- Identifying call and messaging fraud, including robocalls, voice phishing (vishing), and SMS-based scams.
- Authenticating users with biometric AI models to prevent account takeovers.
- Blocking subscription fraud by analyzing sign-up patterns and identifying fraudulent behavior.
AI-driven fraud prevention minimizes financial losses, protects customers from scams, and enhances trust in telecom providers.
4. Securing 5G and Emerging Telecom Technologies
With the rollout of 5G networks, IoT expansion, and edge computing, new security vulnerabilities have emerged. AI plays a crucial role in safeguarding these technologies by:
- 5G Network Protection: AI enables automated risk assessment of 5G network slices, preventing attackers from infiltrating different virtual network segments.
- IoT Device Security: AI detects and mitigates IoT-based threats, preventing botnet attacks and unauthorized device access.
- Edge Computing Protection: AI enhances security at the edge by monitoring decentralized data processing environments.
Telecom operators must integrate AI-powered security strategies into their 5G and IoT infrastructure to maintain resilience against cyber threats.
5. Ensuring Compliance with Data Security Regulations
Telecom operators handle vast amounts of sensitive customer data, making compliance with global data protection regulations essential. AI assists in:
- Automating compliance monitoring, ensuring adherence to laws such as GDPR, CCPA, and FCC guidelines.
- Enforcing access controls and encryption, protecting data from unauthorized use.
- Conducting risk assessments to identify and address security gaps proactively.
By integrating AI-driven data governance and privacy-by-design principles, telecom companies can ensure regulatory compliance while minimizing legal liabilities.
6. Securing the AI Lifecycle in Telecom Security
AI-powered security systems must be protected throughout their lifecycle, from development to deployment. AI security frameworks include:
| AI Lifecycle Stage | Security Measures |
|---|---|
| AI Supply Chain | Secure AI components with access controls, audits, and encryption. |
| Model Training & Inference | Use high-quality, tamper-resistant training data and secure ML pipelines. |
| MLSecOps Practices | Implement AI security best practices, secure deployment protocols, and compliance frameworks. |
| Continuous Monitoring | Regularly test, audit, and update AI models to prevent evolving threats. |
A robust AI security framework ensures that AI-powered defenses remain secure and effective against cyber threats.
7. AI-Powered Real-Time Monitoring and Automated Response
AI-driven real-time monitoring and automated security response enable telecom providers to detect, investigate, and mitigate cyber threats efficiently. These capabilities include:
| AI Capability | Purpose |
|---|---|
| Anomaly Detection | Identifies suspicious patterns in network traffic, user behavior, and system logs. |
| Predictive Security | Forecasts potential threats before they materialize, enabling preemptive action. |
| Automated Security Responses | Enhances IDS/IPS systems with real-time threat response and self-healing capabilities. |
| Fraud Detection | Detects fraudulent activities and blocks unauthorized access in real-time. |
With real-time AI-driven analytics, telecom operators can reduce response times and mitigate damage from cyberattacks.
8. Future Trends: AI Innovations in Telecom Security
As cyber threats evolve, AI security in telecom will continue to advance with emerging technologies such as:
- Blockchain and Federated Learning: Enhancing secure data sharing while protecting user privacy.
- Explainable AI (XAI): Ensuring transparency in AI decision-making to improve trust and accountability.
- Quantum-Resistant Encryption: Preparing telecom networks for post-quantum cybersecurity threats.
Telecom companies must stay ahead of these advancements to maintain a resilient security posture.
Why AI is Essential for the Future of Telecom Security
AI is transforming telecom security, offering real-time threat detection, fraud prevention, compliance automation, and advanced risk mitigation. With the increasing sophistication of cyberattacks, AI-driven security frameworks are essential to safeguard telecom networks and customer data.
To stay ahead of evolving threats, telecom operators must:
- Invest in AI-powered adaptive security to detect and respond to cyber threats in real-time.
- Prioritize data privacy and compliance to ensure regulatory adherence.
- Adopt AI-driven monitoring and automation to enhance security resilience.
As telecom security challenges grow, AI will remain the cornerstone of a proactive, intelligent, and robust defense strategy.